Get comprehensive question and answer solutions for Class 7 Computer book, covering essential topics in computer science. Our carefully crafted resource offers in-depth explanations and insights to help students understand and master key concepts. From hardware components to software applications, programming basics to internet safety, this Class 7 Computer book question answer guide provides clarity and enhances learning. With a focus on problem-solving and critical thinking skills, students can strengthen their understanding and excel in the subject.
Accessible and engaging, our question answer solutions support students in building a strong foundation in computer literacy and preparing them for the digital world. Boost your knowledge and ace your Class 7 Computer exams with our expertly crafted question answer guide.
For more details about computer related topics click given link https://knowledgesthali.com/category/computer/
Chapter 1 Number System
Answer the following questions (Class 7 Computer):
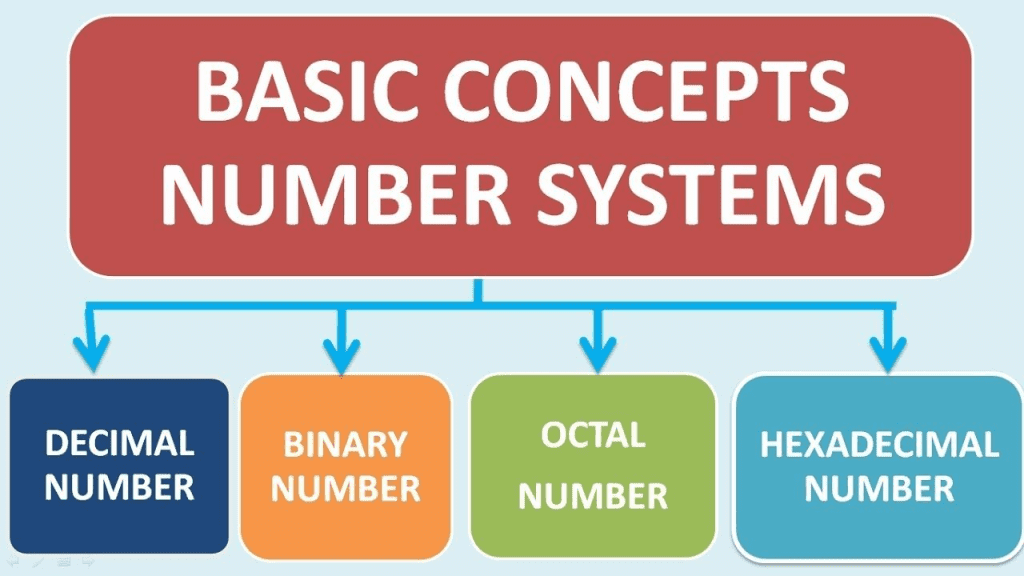
Question 1 : What is number system? Explain its types.
Answer : A number system is a set of values used to represent different quantities.
There are four types of number systems:
- Decimal Number System: Decimal Number System consists of 10 digits from Oto 9. These 10 digits can be used to form any number. It has a base value 10.
Example: (915)10, (153)10
- Binary Number System: Binary Number System consists of 2 digits i.e. 0 and 1. Therefore, it has a base value 2. All the digital computers use binary number system and converts the decimal number format to binary equivalent.
Example: (10011)2, (10001111)2
- Octal Number System: Octal Number System consists of 8 digits from 0 to 7.Therefore, it has a base value 8.
Example: (426)8, (312)8
- Hexadecimal Number System: Hexadecimal Number System consists of 16 digits from Oto 9 and the letters A to F. A- F represents numbers 10 to 15. It has a base value 16. It has a base value 16 because hex = 6 and Decimal = 10 and combining them makes the hexadecimal = 16.
Example: (4A161)16, (3B4)16
Question 2 : How Decimal number converted Into a binary number.
Answer : To convert numbers from decimal to binary
- Divide the given decimal number with the base 2.
- Write down the remainder and divide the quotient again by 2.
- Repeat the step 2 till the quotient is zero.
- Write the reminder
Example: Convert the decimal number 1310 to binary.
Solution: We will start dividing the given number (13) repeatedly by 2 until we get the quotient as 0. We will note the remainders in order.
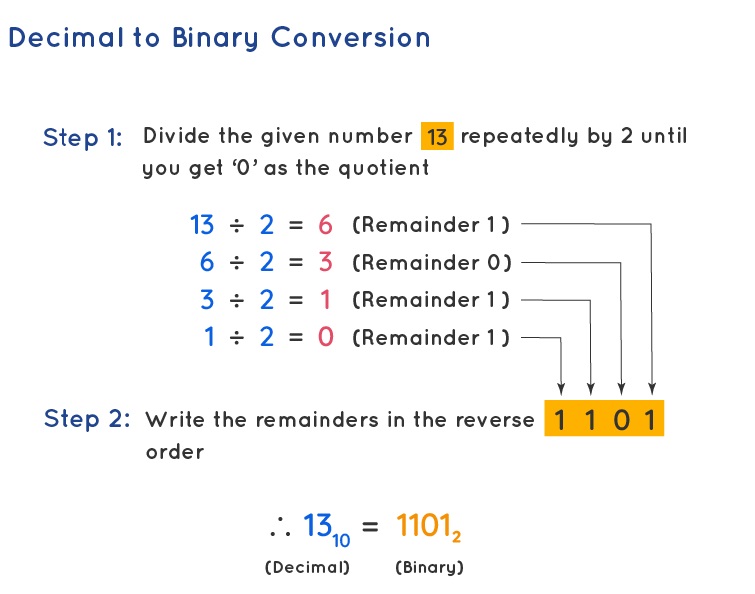
| Division by 2 | Quotient | Remainder |
|---|---|---|
| 13 ÷ 2 | 6 | 1 |
| 6 ÷ 2 | 3 | 0 |
| 3 ÷ 2 | 1 | 1 |
| 1 ÷ 2 | 0 | 1 |
Question3 : Write the rules to subtract two binary number.
Answer : There are four rules of binary subtraction which are:
- 0 – 0 = 0.
- 0 – 1 = 1 ( with a borrow of 1)
- 1 – 0 = 1.
- 1 – 1 = 0.
Chapter 2 Chart in MS Excel
Answer the following questions (Class 7 Computer):
Question 1 : What do you know about chart ? Why are chart useful?
Answer : A chart is used to represent the data graphically. Charts are often used to ease understanding of large quantities of data and the relationships between parts of the data. Charts can usually be read more quickly than the raw data.
Question 2 : Describe some common type of chart.
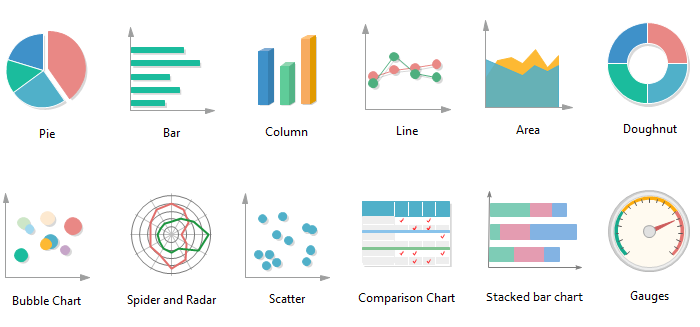
Answer : These are some common types of chart
- Column Chart : A Column Chart typically displays the categories along the horizontal (category) axis and values along the vertical (value) axis.
- Line Chart : Line charts can show continuous data over time on an evenly scaled Axis.
- Pie Chart : Pie charts show the size of items in one data series, proportional to the sum of the items.
- Doughnut Chart : A Doughnut chart shows the relationship of parts to a whole. It is similar to a Pie Chart with the only difference that a Doughnut Chart can contain more than one data series, whereas, a Pie Chart can contain only one data series.
- Bar Chart : Bar Charts illustrate comparisons among individual items.
- Area Chart : Area Charts can be used to plot the change over time and draw attention to the total value across a trend.
- XY (Scatter) Chart : XY (Scatter) charts are typically used for showing and comparing numeric values, like scientific, statistical, and engineering data.
- Bubble Chart : A Bubble chart is like a Scatter chart with an additional third column to specify the size of the bubbles it shows to represent the data points in the data series.
- Stock Chart : a Stock chart can also be used to show fluctuations in other data, such as daily rainfall or annual temperatures.
- Surface Chart : A Surface chart is useful when you want to find the optimum combinations between two sets of data.
- Radar (spider) Chart : Radar charts compare the aggregate values of several data series.
- Combo Chart : Combo charts combine two or more chart types to make the data easy to understand, especially when the data is widely varied. It is shown with a secondary axis and is even easier to read.
Question 3 : write the step to modify the label and tittle of a chart.
Answer : To modify the labels and titles of a chart,
- Select the chart.
- Click on Layout tab in ribbon.
- From Labels group, click on Chart Title or Data Labels option.
- From the drop-down menu, select the appropriate option.
- Change the chart title or data label and press Enter key.
Question 4 : write the step to require to change the data in a chart..
Answer : To change the data in a chart
- Select the chart.
- Click on Design tab in ribbon.
- From Data group, click on Select Data option.
- A Select Data Source dialog box appears.
- Make the desired modifications and click OK button.
Explain the difference between the following terms:
X-axis and Y-axis : X-axis is the horizontal axis, also known as Category axis which represents the categories on the plot area. Y-axis is the vertical axis, also known as Value axis which represents the value of the categories using which a chart is created.
Chart title and Axis title : Chart title is a title given to a chart and axis title is the title of x-axis and y axis.
2D chart and 3D chart : A 2D chart has only two dimensions say length and height, but 3D chart has three dimensions say length, height and width.
Plot area and chart area : A plot area contains only the graphical representation of chart. But chart area includes the plot area and other elements of chart.
Column chart and Line chart : A column chart uses bars that run vertical to plot a chart but line chart uses lines to plot a chart of data series.
Bar chart and Pie chart : Bar chart uses bars that run horizontal to plot a chart but pie chart using one series of data.
Area chart and XY Scatter chart : Area Charts can be used to plot the change over time and draw attention to the total value across a trend but XY (Scatter) charts are typically used for showing and comparing numeric values, like scientific, statistical, and engineering data.
Layout Tab and Format Tab : Format tab can be used to format a chart by changing the styles, adding colors, inserting shapes and changing size, whereas the Layout tab can be used to change the chart layout by adding or modifying chart labels.
Chapter 3 More on Flash CS6
Answer the following questions (Class 7 Computer):
Question 1 : What do you know about flash ? How can you open Flash document and set its properties ?
Answer : A Flash is a multimedia graphic program developed by Abode Systems. It is used to create animations, games, cartoons, graphics and special effects.
Create a new project or open an existing Flash document by selecting “File” > “Open” from the menu or using the CTRL+O keyboard shortcut.
Once the Flash document is open, we can modify its properties through various panels and options in the software.
To set properties in a Flash document, we can specify attributes such as stage dimensions, frame rate, background color, and document title. Additionally, you can set properties for individual objects within the document, such as their position, size, color, transparency, and animation effects.
Question 2 :What do you understand by Gradient. Explain its type in detail.
Answer : A gradient is a multicolor fill in which one color gradually turns into another color. It is a visual effect where colors blend gradually, creating a smooth progression from one color to another. Gradients refers to a smooth transition between two or more colors or shades. There are mainly two types of Gradients: Linear Gradient and Radial Gradient.
In the context of computer graphics and design, these two gradient are used mostly.
- Linear Gradient: Linear gradient changes color from the starting point to end point in a straight line.
- Radial Gradient: Radial gradient changes color in a circular outward direction, starting from the focal point.
There are several types of gradients commonly used in design:
- Linear Gradient: This type of gradient involves a smooth transition of colors along a straight line. It can be horizontal, vertical, or at any angle. Linear gradients can be defined by specifying the starting and ending points, as well as the colors and their positions along the line.
- Radial Gradient: Radial gradients radiate from a central point outward. The transition occurs in a circular or elliptical pattern. Typically, you define a center point, a radius, and color stops that indicate the colors and their positions within the gradient.
- Angular Gradient: Angular gradients blend colors in a circular pattern around a central point. The transition occurs in a clockwise or counterclockwise direction. Similar to radial gradients, you specify a center point and color stops to define the colors and their positions within the gradient.
- Noise Gradient: A noise gradient adds a level of randomness or noise to the transition between colors. It introduces subtle variations, creating a more textured or organic appearance.
- Conical Gradient: Conical gradients blend colors in a circular pattern around a central point, similar to angular gradients. However, instead of a smooth transition, they create a series of concentric color bands or rings.
Question 3 : Explain the purpose of following component :
- Property inspector
- Timeline
- Layers Panel
- Tool Panel
Answer :
- Property Inspector: A property inspector is used to organize and modify the properties of the current selection.
- Timeline: A timeline is used to organize and control a file content over time in layers and frames.
- Layers Panel: A layer panel is used to manage the layers. Layers are like multiple film strips stacked on top of other, each containing different image that appears on stage.
- Tools Panel: A tools panel is used to display various tools from which you can choose any according to your requirements. It includes Selection, Sub selection, Lasso, Pen, Line etc.
Question 4 : How will you Import Graphics From another file ?
Answer : To import graphics from another file,
- Click on File menu.
- From drop-down list, select Import> Import to Stage.
- An Import dialog box appears.
- Browse and select the file that you want to import on stage in Flash.
- Click OK button.
Question 5 :What do you mean by animation? explain its types of animation.
Answer : Animation is an illusion of the movement of a series of still images appeared in rapid sequence. This transition from one image to another is so quick that it seems to be a movie.
Types of Animation:
- Frame-by-Frame animation: In this type of animation, an image is made in every frame with slight modifications in the image.
- Tweened Animation: In this type of animation, the starting and ending keyframes are formed to animate the object. Flash itself gives the motion effect in between the frames.
Question 6 : Explain the utility of Filter in Flash .
Answer : Filters are used to add interesting visual effects to text, buttons and movie clips. They generally include effects like Drop Shadow, Blur, Glow, Bevel etc. These effects can be applied using Properties Panel. To apply filters to the text,
- Select the Text tool and enter some text on stage in Flash document.
- Select Selection tool and go to Modify> Break apart.
- Now, convert each letter of the text into symbol by pressing F8.From Convert to Symbol dialog box, select ‘Movie Clip’ type.
- Use Selection tool and select all the letters of the text.
- From the lower left corner of Properties Panel, select Add Filter button under Filter section.
- Select any filter say Drop Shadow from Context menu and observe the change.
Question 7 : How can you edit objects in flash?
Answer: In Flash you can edit an object by transforming its shape, scaling, skewing or rotating an object.
To edit objects in Flash, follow these steps:
- Select the object you want to edit by clicking on it.
- Use the selection tools to resize, rotate, or move the object.
- Modify the object’s properties, such as color, transparency, or effects, using the Property Inspector or related panels.
- Double-click on the object to enter its edit mode. This allows you to modify the object’s contents, such as text, shape, or symbols.
- Use the drawing tools, text tools, or other editing features to make changes to the object.
- Exit the edit mode by clicking outside the object or pressing the Escape key.
Please note that Flash has been discontinued and is no longer supported by Adobe. It has been replaced by Adobe Animate, which offers similar functionality for editing objects.
Chapter 4 Working with Layers
Answer the following questions (Class 7 Computer):
Question 1 : What do you know about Layer? How can you add a new Layer and change its name?
Answer : In graphic design and animation software like Adobe Flash (now known as Adobe Animate), layers are used to organize and manage different elements of a project. Each layer can contain various objects, such as graphics, animations, text, or sound, and they are stacked on top of each other to create a composite image.
To add a new layer in Adobe Flash (Adobe Animate) and change its name, we can follow these steps:
- Open our Flash document in Adobe Flash (Adobe Animate).
- Locate the “Layers” panel, typically located on the right side of the software interface. If we don’t see the panel, we can go to “Window” > “Layers” to make it visible.
- In the “Layers” panel, we will see a list of existing layers. To add a new layer, click on the “New Layer” button at the bottom of the panel. This will create a new layer above the currently selected layer.
- By default, the new layer will be named “Layer X,” where X represents a numerical value. To change the name of the layer, double-click on the layer’s name in the “Layers” panel. Alternatively, we can right-click on the layer and select “Properties” from the context menu to access the layer properties, including the name field. Enter the desired name for the layer and press Enter or click outside the name field to apply the change.
Repeat these steps to add additional layers and customize their names as needed.
Question 2 : What do you know about hiding and showing a layer? How will you lock a layer?
Answer : In Adobe Flash (Adobe Animate) or similar software, we can hide or show layers to control the visibility of the elements contained within those layers. Additionally, we can lock a layer to prevent accidental modifications or movements of its contents. Here’s how we can perform these actions:
- Hiding and showing a layer:
- Locate the “Layers” panel in Adobe Flash (Adobe Animate).
- Find the layer you want to hide or show.
- In the “Layers” panel, there is usually an eye icon next to each layer. Clicking on this eye icon will toggle the layer’s visibility. If the eye icon is visible (not crossed out), the layer is visible; if it’s crossed out, the layer is hidden. Clicking on the eye icon will switch between these states, allowing you to hide or show the layer accordingly.
- Locking a layer:
- In the “Layers” panel, locate the layer we want to lock.
- Look for a padlock icon next to the layer. Clicking on this padlock icon will toggle the layer’s lock state. If the padlock is closed, the layer is locked; if it’s open, the layer is unlocked.
- When a layer is locked, we cannot select or modify the objects within that layer. This can be useful to protect specific elements from accidental changes while working on other parts of the project. To make modifications to a locked layer, we need to unlock it first.
Question 3 : What Onion Skinning? Explain in detail.
Answer : Onion Skinning is used to create a faint ghost image of the previous frame. By clicking on Onion Skin option, we can view numbers of several frames before and after the current frame. There are two types of Onion Skinning:
- Onion Skin: It displays the frame in full color.
- Onion Skin Outlines: It displays only the outlines of the objects in a frame.
Question 4 : What do you understand by Masking in Flash?
Answer : Masking is used to create a spotlight effect that would display the text or object through a hole. It uses a shape to hide or reveal portions of a piece of artwork. It is just like viewing the outside through a small window in your house. It is a way for we to control the content that our audience sees. In Flash, we put a mask on one layer and the content that is masked is on the layer below it.
Chapter 5 Introduction to HTML
Answer the following questions (Class 7 Computer):
Question 1 : What do you understand by HTML? Explain the HTML Document structure.
Answer : HTML is a Hyper Text Markup Language which is used to create web pages. It is a complete package code using which users can generate web pages that consists of both text and graphics. The document structure of HTML is given below:
| <html> <head> <title> Title of a webpage </title> </head> <body> Body of the document </body> </html> |
The general structure of HTML document has two parts: Head and Body.
- Head Section: Head section contains the general information like title of web page.
- Body Section: Body section contains the contents which will be displayed on the web page. The body of the webpage is defined using various tags and attributes.
Question 2 : What are Container and Empty Elements in HTML? Explain with the help of examples.
Answer :
- Container elements: Container elements are HTML elements that can contain other elements or text within them. They have an opening tag, a closing tag, and the content placed between the opening and closing tags. Examples of container elements include
<div>,<p>,<ul>,<table>,<section>, etc.- For example: <b> This element is used to bold the enclosed text. </b>
- Empty elements: Empty elements are those elements which include only ON tag. These elements start with starting tag or ON tag, but has no ending tag or OFF tag. Examples of empty elements include
<img>,<br>,<input>,<hr>,<meta>, etc.
Question 3 : What is HTML Editor? Write the steps to create a web page in HTML.
Answer : An HTML editor is a software tool used for creating, editing, and managing HTML documents. It provides an interface that simplifies the process of writing HTML code by offering features such as syntax highlighting, code suggestions, auto-completion, and a preview of the rendered web page.
There are two most common types of editors used, WYSIWYG editor and Text editor.
- WYSIWYG editor: WYSIWYG expands to What You See Is What You Get editor. It allows the users to do editing directly in a web browser. It does not require the knowledge of HTML while using this editor.
- Text editor: To use Text editor, you must have a thorough knowledge of HTML
Steps to create a web page in HTML are:
- Click on Start> All apps> Windows Accessories> Notepad.
- A Notepad window opens.
- Type the HTML code.
- Go to File> Save As option. A Save As dialog box opens.
- Type the file name and save with extension .html. Click on Save button.
Question 4 : Explain any two Container tags and two Empty tags with example.
Answer : The explanation of two container tags are given below:
- <p>: <p> is a paragraph tag which has an ending tag i.e. </p>. It is used to mark the block oftext as a paragraph in a web page. When you start a new paragraph, the web browser will leave one line between the two paragraphs.
- Syntax:< p> Paragraph text </p>
- Example: <p> Internet has become an integral part of our lives. It is a network of networks in which user at one computer can get the information from any other computer provided he must have a permission. </p>
- <b>: <b> is a bold tag which is used to emphasize the enclosed text by making it bold.
- Syntax: <b> Text </b>
- Example: <b> This is used to make the text bold. </b>
The explanation of empty tags are given below:
- <br>: <br> is a line break tag which is used to move the followed text to the next line. It works like an Enter key of the keyboard.
- Syntax: <br>
- Example: <br>
- <hr>: <hr> is a horizontal rule tag which is used to draw a horizontal line along the page.
- Synatx: <hr>
- Example: <hr>
Question 5 : What are Cascading Style Sheets? Name the different methods available for applying Style rules.
Answer : Cascading Style Sheets or CSS are used to format the layout of web pages and their visual formatting. It makes it easy to change styles across several web pages at once. Using CSS, the display of the document can be separated with the contents of the document. The various methods of using CSS are:
- External CSS: In this method, the style rules are defined individually in one file which can be used with any HTML document. External CSS is a text file with extension .css. To link this file, you need to give the reference of the file using <link> tag in head section.
- Internal CSS: In this method, the style rules are defined inside the <style> element in the head section.
- lnline CSS: In this method, you can add the style attribute to the relevant element, which may contain any CSS property.
Question 6 : Explain the various background properties of cascading Style sheet with syntax.
Answer : The various Background properties of CSS are:
- Background color: This property is used to set the background color of a HTML element.
- Syntax: background-color: color or RGB code Background image:
- This property is used to set an image to the HTML document
- Syntax: background-color: color or RGB code Background image:
- Background image: This property is used to set an image to the HTML document
- Syntax: background-image: url(image.jpg);
- This property is used to set an image to the HTML document
- Syntax: background-image: url(image.jpg);
- Background Position: This property is used to set the position of the image on the HTML document.
- Syntax: background-position: value
- Background Repeat: This property is used to set the repetition pattern of an image on the webpage, like repeat the image horizontally or vertically or both or don’t repeat.
- Syntax: background-repeat:value
- Background Attachment: This property is used to either fixing the image in the background or make it scroll when user scrolls the page.
- Syntax: background-attachment: fixed or scroll
Chapter 6 Working with Web Browsers
Answer the following questions (Class 7 Computer):
Question 1 : What do you understand by a web browser? Give examples.
Answer : A web browser is an application software using which you can access to the world wide web. You can use the web browser to open the webpages by specifying the URL in the address bar. It brings the webpages from the servers along with necessary files like images, audio, video, interprets them and then display it in the browsers.
There are two types of browsers:
- Text Web browsers: It displays only text.
- Examples: Lynxlet (Lynx for Mac), w3m, ELinks, Links, Lynx
- Graphic Web browsers: It displays both text and graphics.
- Examples: Internet Explorer, Mozilla Firefox, Microsoft Edge, Google Chrome, Safari
Question 2 : List the popular web browsers Explain any two.
Answer : The various popular web browsers are:
- Internet Explorer,
- Mozilla Firefox,
- Microsoft Edge,
- Google Chrome,
- Safari,
- Opera.
Google chrome: Google Chrome was developed by Google and was released in 2008. It allows its users to quickly access the web pages and make local desktop shortcuts to open web application in the browser.
Internet Explorer: Internet Explorer by developed by Microsoft in 1995. It can be used to view web pages, to listen and watch streaming contents, access online banking, make sale or purchase on internet.
Question 3 : How can you browse, view and delete the history in internet Explorer?
Answer : Every time you browse the internet, your web browser keeps its track and create a history of pages you have seen. These pages will stay in the history for a certain number of days. If you want to view the history in internet explorer, first click on Favorites button and then on History button. If you want to delete the history, click on Favorites button, then on History option and then click on ‘Clear history’ option. The history will be cleared from the browser.
Question 4 : What is search engine? Name two search engines.
Answer : A search engine is a software program which is used to search specific information. For this, you need to specify the keyword related to the search in Search box and press Enter key. It will display the links to the web pages related to the search. You can click on any link and the related web page will open in the browser.
There are various search engines available but the most popularly used search engine is Google. The other available search engines are Bing, Ask and Yahoo.
Question 5 : What do you know about bookmarks?
Answer : Bookmark is a feature of a web browser which is used to save a web page’s address. While browsing the web pages, you can bookmark the current webpage by using Ctrl + D shortcut key. In Internet Explorer, Bookmarks are also referred to as Favorites. It is useful when you want to remember a webpage and want to view it again. Bookmark creates a shortcut for quick access to that webpage. In Internet Explorer, you can access and view the bookmark using shortcut key Ctrl + I.
Question 6 : What is purpose of HTTP protocol?
Answer : The purpose of the HTTP (Hypertext Transfer Protocol) protocol is to facilitate communication between web browsers (clients) and web servers. HTTP is the foundation of data exchange on the World Wide Web and enables the retrieval and delivery of web resources such as HTML documents, images, videos, and more.
When a web address is entered in the address bar of a web browser, the browser sends an HTTP command to the web server. The browser asked the server to respond by transmitting the requested webpages to the client by displaying it on web browser. All the web servers serving websites and web pages support HTTP protocol. Example: https://www.knowledgesthali.com/category/computer/
Here,
- https: is a protocol
- www.knowledgesthali.com/: is server name
- category/computer/: is file name
Chapter 7 Electronic Mail
Answer the following questions (Class 7 Computer):
Question 1 : What do you understand by an e-mail? Write down the various advantages and disadvantages of using email?
Answer : E-mail or Electronic mail is a way to send and receive messages through the internet. You can attach digital files like documents video clips, images, audio files etc. to the email. The mail sent via email service reaches to its destination within few seconds. The most commonly used email services are Gmail, Rediffmail, Yahoo mail, Outlook etc.
Advantages of using Email:
- It is the cheapest mode of sending and receiving messages.
- Sent and received messages are stored in receiver’s inbox which can be checked at anytime.
- It is the fastest method of communication because the message can reach to any part of the world within fraction of seconds.
- You can access this service anytime and from anywhere provided that you must have an internet connection.
- There is no use of paper so thus it reduces environmental cost.
Disadvantages of using Email:
- E-mail is the main source of virus which may be harmful for the computer.
- Due to lack of emotions and facial expression, there may be misunderstanding while interpreting the emails.
- Spam and junk mails are very common.
Question 2 : Write the different steps for attaching a file with an e-mail.
Answer : You can attach a digital file with an email like text files, images, audio or video files etc.
Steps to attach a file to the email are:
- Click on Compose button to compose an email.
- A New Message box opens.
- Type the receiver’s id, subject and message.
- Click on Attachment button. An Insert Attachment dialog box opens.
- Browse and select the file which you want to attach.
- Click Attach button.
- The file will be attached to the email and displayed in New Message box.
- Click Send button to send the mail.
Question 3 : Write the various components of an e-mail window?
Answer : The various components of email window are:
Inbox: It is used to store the received mails.
Compose: It is used to create and send a new message. When you click on Compose button, it contains the following components:
- To: In this textbox, type the email address of recipient.
- Cc (Carbon Copy): In this textbox, type the email address of the recipient to whom you want to send the same copy of mail.
- Bcc (Blind Carbon Copy): It is same as Cc but the email address of recipients will not be visible to each other.
- Subject: It contains the subject of the email.Body of the Mail: It contains the actual message.
- Body of the Mail: It contains the actual message.
- Attachment: It is used to attach the digital document with email.
- Starred: It contains the important mails which are marked as starred.
- Sent Mail: It contains all the mails you have sent to the recipients.
- Drafts: It contains those messages which you do not want to send yet.
- Trash: It is used to store the deleted emails for a defined time.
- All Mail: This is an archive folder where all emails are stored with label.
- Sign out: It is used to sign out from the email account.
Question 4 : What do you understand by Netiquette?
Answer : Netiquettes are the internet etiquettes. It involves respecting other’s privacy and not doing anything that annoy other internet users.
Some of the netiquettes are given below:
- Be courteous and respectful to other online users.
- Use emoticons while communicating to express your emotions.
- Use small letters instead of capital letters as it can be considered as being rude.
- Do not share your personal details with anyone.
- Do not use any one’s personal information without his permission.
- Do not use anyone’s copyright as your own.
Question 5 : How do you create an e-mail account in a free e-mail service provider?
Answer : To create an email account on gmail (for example),
- Open the web browser and type www.gmail.com in address bar.
- Click on Create account option.
- A form will appear which you need to fill like name, date of birth, phone number, gender email address, and password.
- There is a section that includes security questions which can help to retrieve the password in case you forget it.
- In the next section, you need to type a code for security reasons.
- Then click on I Agree option which indicates that you are agreed with all the terms of services.
- Click on Create button and your new email account will be created.
Question 6 : What do you know about blogging? How it can be created?
Answer : A blogging is an act of posting contents on a blog. A blog or weblog is a personal online diary which allows you to share and post your thoughts and ideas. You can also add pictures, audio or video etc. to the blog. It helps the users to interact with each other by posting biogs or adding comments to other’s biogs. A person who is involved in blogging is known as Blogger. There are many types of blogs like personal blogs, corporate blogs, organizational blogs etc.
To create a blog,
- First step in creating a blog is to choose a topic of the blog.
- The topic should be you are interested in or expertise in.
- Create an account.
- Based on the topic you choose, pick a domain that tells readers what your blog is about.
- Customize the design of blog like fonts, color scheme, header image etc.
- Now, create your first blog by clicking on Add button.
- It will direct you to an editor where you can write and format the blog.
- Publish your blog to share it with others.
Chapter 8 Computer Viruses
Answer the following questions (Class 7 Computer):
Question 1 : What do you understand by a computer virus? Name any five computer viruses.
Answer : A computer virus is a type of ill-natured code or program which once enters into the computer, corrupts it and it is designed to enter from one computer to another. A virus has a potential to cause damage effect such as harming the system software or corrupting data. It can enter into the computer through infected CD, pen drive, or internet.
The five computer virus are:
- Resident virus
- Overwrite virus
- Trojans
- Boot virus
- Worms
Question 2 : How do computer virus spread?
Answer : A computer virus normally spreads through emails, instant messages and risky websites. Each time when an infected file is opened, the virus multiplies and spreads to other programs. Some viruses replicate faster and corrupt every file we store in the computer. The performance of the computer is badly affected and maintenance will become difficult. Computer virus generally spreads in one of three ways:
- Through removable media like CD, Pendrive etc.
- Through downloaded files from internet.
- Through email attachments
Question 3 : What is an antivirus software? Give examples.
Answer : An antivirus software is a software program which is used to detect and remove the virus immediately. It is advisable to load an antivirus software in your system to keep your system protected from any malicious program. When you start the computer, antivirus starts automatically. It scans the entire files in the system to detect the virus. If a virus is detected, that virus is removed.
Examples: Norton, AVG, McAfee, Kaspersky, Smart Dog
Question 4 : List the various signs that signify the presence of a virus in our computer.
Answer : The signs that signify the presence of virus in the computer system are:
- The computer starts to operate slower than normal.
- The computer shuts down frequently.
- The computer usually restarts on its own.
- Applications stored in the system do not work as usual.
- Strange error messages might display on the screen.
- Strange icons emerge on the desktop that are not associated to any program.
Question 5 : What are the preventive measures to keep away viruses from the computer
Answer : The preventive measures to keep the virus away from the computer system are:
- Only authorized users must be allowed to access the system.
- You should keep the programs and data on separate disks.
- Before using the removable devices like pen drives or CDs, you should scan the devices.
- Install a latest version of antivirus software in the system.
- Do not open any emails you receive from strangers.
Chapter 9 Cyber Threats & Security
Answer the following questions (Class 7 Computer):
Question 1 : Why there is a need to secure our computer?
Answer : It is important to secure the computer to keep the information protected. A break in computer security may cause harmful and potentially major issues. Proper computer security helps prevent viruses and malware which allows programs to run quicker and smoother.
The various security threats are:
- Installing unverified freeware
- Opening emails from unknown sender
- Using removable disks without scanning
Therefore, it is required to keep your system safe which can be done by keeping the security software updated, enable a firewall, adjust the privacy and security settings of a browser, install antivirus and antispyware software, keep our system protected by using password.
Question 2 : What do you understand by Cyber Crime ? Also, mention the categories.
Answer : Cyber Crime is an unlawful activity done through internet. It may include identity theft in which somebody steal our email-id or password and use it to send fake emails to others like winning lottery or product etc. It may also include credit card account thefts, internet frauds, forgery, harassing others and much more which comes under the jurisdiction of Indian Panel Code (IPC).
Cybercrime can be categorized in to three types:
- Crime against an individual person
- Crime against property
- Crime against an organization/society
Question3 : Write the different between Cyber Stalking and Cyber Bullying. Explain briefly.
Answer : Cyber Bullying is an act to harass or harm a person by posting insulting remarks against gender, race, religion or nationality and sending threatening messages by emails, posting embarrassing photos, emails to hurt someone to threaten him. The attacker is often anonymous or unknown and there is no one to fight back against.
Cyber Stalking is a more specific form of Cyberbullying. It is the use of the internet and other technology to harass someone by spying on them from electronically. Most social media websites have made it easier to keep an eye on someone’s activities. The purpose of Cyber Stalking is to gather information about the person or humiliate the victim or his family by posting false information about him.
Question 4 : What do you know about the term Phishing ?
Answer : Phishing is a form of fraud in which an attacker acts like a reputable entity or person in email or other communication channels. The user is asked to visit a website in which he needs to enter his personal information like username, password, credit card details etc.
Like, sometimes it happens that you get a mail like you are winning an award or money type mails, in which you are asked to enter your login details or credit card details or OTP (One Time Password).
In this way, the operators of the fake website conduct crimes in your name after stealing your identity like to attack on the bank property and steal money. While using the internet, you may find various counterfeit websites resembles to the authorized sites, in which when you enter the personal and confidential details, are recorded on the wicked person’s system and he can use for his benefits.
Question 5 : What is identity theft ? Explain briefly.
Answer : Stealing someone’s personal information is called Identity Theft. It is a major issue for people who use internet for online shopping, cash transactions and banking services. an imposter steals the identity of another person like name, photograph, signature, email id, id card, etc. and use it for nasty reasons. By using the identity details of another person, he can steal his property, purchase something on his name, send wicked messages from his id, commit crimes using his name and photograph, share his identity and phone number publicly, which may cause big harm to his reputation. The stolen information generally includes the person’s name, date of birth, account number, credit/debit card number, ATM pin etc.
Question 6 : What points should be kept in mind while cresting a password ?
Answer : While creating a password, a person should keep the following points in mind.
- A password should start and end with special characters.
- It should be more than 8 characters.
- It should not be common like date of birth or on pet name.
- It should be strong and unique.
Question7 : Explain data backup. What is the advantage of taking a backup ?
Answer : A data backup is referred to the process of making copies of data or data files on some secondary storage. It is advisable to keep the backup of the data. It is useful in case when the original data or data files are lost or destroyed, you can retrieve the data from the data backup.
Question 8 : What is firewall ? Why do we use it for our computer ?
Answer : Firewall is a security system which is used to protect computer by preventing unauthorized users from accessing the system through internet. It can either be hardware or software or combination of both. It is enacted on the gateway of a network and follows a particular set of rules defined by user or network administrator. On the basis of these rules, it checks the incoming and outgoing network traffic. And allows only the authorized packets to enter into the network.
Chapter 10 Introduction to Python
Answer the following questions (Class 7 Computer):
Question 1 : Define Python.
Answer : Python is one of the most powerful high level programming language. It is an interpreted object-oriented programming language that has gained popularity. It was created by Guido van Rossum.
Question 2 : Define data type in Python
Answer : Data type means the type of data stored in a variable. Each language has it’s own data type to store data in variable. Python also has many data types.
| Data Type | Description |
|---|---|
| int (integer) | It represents a number without a fractional part, i.e., no decimal point is used. For example, a=50, b=99, c=251 etc. |
| float | It represents a number with fractional part i.e., a decimal point is used to seprate the integer and fractional parts. For example x=70.2, y=99.25 etc. |
| str (string) | It represents a string a string of characters enclosed within single quotes (‘) or double quotes (“). For example “Hello”, ‘Python’, “99” etc. |
Question 3 : Write some applications of the python language in the contemporary world.
Answer : Following are application of the python language:
- Web Development.
- Game Development.
- Scientific and Numeric Applications.
- Artificial Intelligence and Machine Learning.
- Software Development.
- Enterprise-level/Business Applications.
- Education programs and training courses.
- Language Development.
Question 4 : Write rules to name a variable.
Answer : Rules to name a variable :
- The name of the variable can only begin with a letter (a-z, A-Z) or an underscore (_).
- All variable name are case senstive.
- Variable name cannot contain punctuation characters like (&, %, *,) etc.
- Name your variables based on the terms of the subject area, so that the variable name clearly describes its purpose.
- Create variable names by deleting spaces that separate the words.
- Do not begin variable names with an underscore.
- Do not use variable names that consist of a single character. Short variable names are only allowed for loop counters.
- Name variables that describe binary states (“true” or “false”) after the state that matches the “true” value.
Question 5 : How will you change an entered value using the input() function into the integer type?
Answer : From the following way, We change an entered value using the input() function into the integer type :
- Whenever an input is taken in python, the input() function converts the line to string.
- To change the entered value to integer type, we use int() function.
- The int() function returns the integer object from any number or string.
- For example, when we want to input a number, say n, we can write the given códe like this n = int(input(“Enter a number: “))


Thank you sir
This is a very useful website
Welcome Shivansh
Thank you sir
Welcome Divyanshu
Thanks sir
Welcome Adarsh
Thank you sir
Welcome Danish
Thanks sir 😊
This is very useful website
This is very useful website sir
I’m not sure where you’re getting your information, but good topic.