The crime that involves and uses computer devices and Internet, is known as Cyber Crime.
Cyber Crime can be committed against an individual or a group; it can also be committed against government and private organizations. It may be intended to harm someone’s reputation, physical harm, or even mental harm.
Cyber Crime can cause direct harm or indirect harm to whoever the victim is. However, the largest threat of cyber crime is on the financial security of an individual as well as the government. Cybercrime causes loss of billions of USD every year.
Types of Cyber Crime
There are three major categories of cyber crimes:
- Crime against an Individual Person
- Crime against Property
- Crime against an Organization /Society
1. Crime against an Individual Person
These crimes include cyber harassment and stalking, distribution of child pornography, credit card fraud, human trafficking, spoofing, identity theft, and online libel or slander. These crimes can be committed in the form of :
- Cyber Bullying
- Cyber Stalking
- Child Pornography
- E-mail Spoofing
- SMS Spoofing
Cyber Bullying (Cyber Crime)

Cyberbullying is an act of sending, posting or sharing negative, harmful, false or demeaning content regarding others. Sharing personal or private information which could cause embarrassment or humiliation to others too falls under the ambit of Cyberbullying. It takes place through digital devices such as cell phones, computers, and tablets via services such as SMS, texts, Apps, social media platforms, online forums and gaming where people can view, participate or share content.
Cyber Stalking (Cyber Crime)

Cyber stalking is the usage of Information and Communications Technology (ICT) to stalk, control, manipulate or habitually threaten a minor, an adult or a business group. Cyberstalking is both an online assailant tactic and typology of psychopathological ICT users. Cyberstalking includes direct or implied threats of physical harm, habitual surveillance and gathering information to manipulate and control a target. Table 3 describes the various means of ICT, motives behind their usage and the various targets.
Child Pornography (Cyber Crime)

Child pornography is pornography that exploits children. It is against the law in many countries. Child pornography is made by taking pictures or videos, or more rarely sound recordings, of children who are wearing less clothing than usual, wearing no clothing, or being raped. It can also be made using illustrations of children. Child pornography is sometimes called “child sexual abuse images” because it is images (pictures) of a child who is being sexually abused. Child pornography can be made by setting up a camera or other recording device and molesting a child.
E-mail Spoofing (Cyber Crime)

Email spoofing is a technique used in spam and phishing attacks to trick users into thinking a message came from a person or entity they either know or can trust. In spoofing attacks, the sender forges email headers so that client software displays the fraudulent sender address, which most users take at face value. Unless they inspect the header more closely, users see the forged sender in a message. If it’s a name they recognize, they’re more likely to trust it. So they’ll click malicious links, open malware attachments, send sensitive data and even wire corporate funds.
SMS Spoofing (Cyber Crime)
Cybersecurity attacks are increasing rapidly. Phishing and similar fraud like spoofing was the most prevalent type of cybercrime reported to the U.S. Internet Crime Complaint Center in 2021, affecting almost 324 thousand people.
You get a text from someone you believe to know, but something doesn’t seem right upon closer inspection. The name and mobile number are not identical to those in people’s contact lists; they are just similar.
Cybersecurity attacks are increasing rapidly. Phishing and similar fraud like spoofing was the most prevalent type of cybercrime reported to the U.S. Internet Crime Complaint Center in 2021, affecting almost 324 thousand people. SMS spoofing works by disguising the real sender’s phone number in an SMS message so that it appears to come from a different device. This can be done in two ways:
- We can send an SMS message from our victim’s phone to someone we want to communicate with. This will trick the recipient into thinking the message comes from someone we know, such as a friend or colleague.
- We can send an SMS message from another person’s phone number to someone you want to communicate with. This will also trick the recipient into thinking the message comes from someone else, such as a friend or colleague.
2. Crimes Against Property
Some online crimes occur against property, such as a computer or server. These crimes include DDOS attacks, hacking, virus transmission, cyber and typo squatting, computer vandalism, copyright infringement, and IPR violations.
In real life, we hear of stealing or robbing of one’s property. In cyber world also, criminals look for an opportunity to steal or rob through Internet. They can steal a person’s bank details and withdraw money from his account, misuse credit card of a person, spoil the system of an organization through malicious software to gain access tp it.
- Identity Theft
- Phishing
- Pharming
- Intellectual Property Crime
Identity Theft (Cyber Crime)
Identity theft is the crime of obtaining the personal or financial information of another person to use their identity to commit fraud, such as making unauthorized transactions or purchases. Identity theft is committed in many different ways and its victims are typically left with damage to their credit, finances, and reputation.
- Identity theft occurs when someone steals your personal information and credentials to commit fraud.
- There are various forms of identity theft, but the most common is financial.
- Identity theft protection is a growing industry that keeps track of people’s credit reports, financial activity, and Social Security Number use.

Identity theft occurs when someone steals your personal information—such as your Social Security Number, bank account number, and credit card information. Identity theft can be committed in many different ways. Some identity thieves sift through trash bins looking for bank account and credit card statements.
More high-tech methods involve accessing corporate databases to steal lists of customer information. Once identity thieves have the information they are looking for, they can ruin a person’s credit rating and the standing of other personal information
Phishing (Cyber Crime)

Phishing attacks are the practice of sending fraudulent communications that appear to come from a reputable source. It is usually done through email. The goal is to steal sensitive data like credit card and login information, or to install malware on the victim’s machine. Phishing is a common type of cyber attack that everyone should learn about in order to protect themselves.
Sometimes attackers are satisfied with getting a victim’s credit card information or other personal data for financial gain. Other times, phishing emails are sent to obtain employee login information or other details for use in an advanced attack against a specific company. Cybercrime attacks such as advanced persistent threats (APTs) and ransomware often start with phishing. Some types of fishing is given by:
Deceptive phishing (Cyber Crime)
Deceptive phishing is the most common type of phishing. In this case, an attacker attempts to obtain confidential information from the victims. Attackers use the information to steal money or to launch other attacks. A fake email from a bank asking you to click a link and verify your account details is an example of deceptive phishing.
Spear phishing (Cyber Crime)
Spear phishing targets specific individuals instead of a wide group of people. Attackers often research their victims on social media and other sites. That way, they can customize their communications and appear more authentic. Spear phishing is often the first step used to penetrate a company’s defenses and carry out a targeted attack.
Whaling (Cyber Crime)
When attackers go after a “big fish” like a CEO, it’s called whaling. These attackers often spend considerable time profiling the target to find the opportune moment and means of stealing login credentials. Whaling is of particular concern because high-level executives are able to access a great deal of company information.
Pharming (Cyber Crime)
Similar to phishing, pharming sends users to a fraudulent website that appears to be legitimate. However, in this case, victims do not even have to click a malicious link to be taken to the bogus site. Attackers can infect either the user’s computer or the website’s DNS server and redirect the user to a fake site even if the correct URL is typed in.

Pharming is a scamming practice in which malicious code is installed on a personal computer (PC) or server, misdirecting users to fraudulent websites without their knowledge or consent. The aim is for users to input their personal information. Once information, such as a credit card number, bank account number or password, has been entered at a fraudulent website, criminals have it, and identity theft can be the end result.
Pharming uses the domain name system (DNS) to redirect users from the intended domain to another website. This can be done by exploiting vulnerabilities in the DNS protocol or by compromising insecure DNS servers and adding entries that redirect traffic.
The DNS server translates domain names, such as google.com, to Internet Protocol (IP) addresses, such as 187.128.30.49. If the IP address of a website in the DNS server is changed by a pharmer, then the computer will have the wrong — or corrupted — IP address when accessing that website. By causing the DNS server to give the user the incorrect answer, the pharmer can send users to a fake site for some nefarious purpose.
Difference between Pharming and Phishing
Pharming has been called “phishing without a lure.” In phishing, the perpetrator sends out legitimate-looking emails — appearing to come from some of the web’s most popular sites — in an effort to obtain personal and financial information from individual recipients. But, in pharming, larger numbers of computer users can be victimized because it is not necessary to target individuals one by one, and no conscious action is required on the part of the victim.
Phishing is an attempt to extract sensitive information, such as usernames, passwords and credit card details, by masquerading as a trustworthy entity in an electronic communication. Phishing is typically carried out by email spoofing or instant messaging (IM), and it often directs users to enter details at a fake website, whose look and feel are almost identical to the legitimate one.
Phishing is a numbers game: If a hacker sends out 1 million phishing emails, they may get only a handful of responses — but those responses can still be valuable. For example, a hacker may not get every bank password from a single phishing email, but if they can get one response out of 10,000 unsuspecting victims, their scam succeeded.
Pharming, on the other hand, is a form of phishing that uses a DNS system to send a user to a fake website. Instead of sending an email that looks like it’s from a user’s bank, pharming directs victims to a website that looks like their bank’s website.
Intellectual Property Crime

Intellectual property (IP) crime comes in many forms, but it generally involves counterfeiting (infringement of trade marks) and piracy (infringement of copyright). IP crime can relate to digital or physical products:
Digital IP crime :
This is criminal activity related to digital formats which are protected by copyright, including music, films, software and video games. It covers both copying and distribution of digital files carried out in the course of business, or carried out to such a degree that it has a prejudicial impact.
Physical IP crime :
This is criminal activity relating to the counterfeiting of physical products and the infringement of trade marks by copying the branding. It covers a wide range of items from pharmaceuticals and healthcare products to pesticides, tobacco and alcohol, industrial products such as Aeroplane spare parts and luxury goods. Physical IP crime also includes copyright piracy of non-digital products such as books, CDs and DVDs.
3. Crime against an Organization /Society
When a cybercrime is committed against the government, it is considered an attack on that nation’s sovereignty. Cybercrimes against the government include hacking, accessing confidential information, cyber warfare, cyber terrorism, and pirated software.
- Cyber Vandalism /Digital Vandalism
- Hacking
- Cyber Squatting
- Forgery
- Cyber Extortion
- Cyber Terrorism
Cyber Vandalism/Digital Vandalism (Cyber Crime)

Destructive cyberattacks without any obvious profit or ideological motive. Cyber vandals can deface websites, disrupt a company’s services, or delete databases.
Cyber vandalism is damage or destruction that takes place in digital form. Instead of keying someone’s car, cyber vandals may deface a website (such as Wikipedia), create malware that damages electronic files or elements that interrupt its normal utilization, or remove a disk drive to disable a computer system.
Digital Vandalism, where the purpose is to steal and misuse data, digital vandalism only seeks to damage, destroy, or disable data, computers, or networks. Cyber vandalism can impact businesses drastically, including the ability of your customers to access services as well as financial loss or impact to your brand or reputation. In the next section, we’ll highlight some common forms of vandalism that cyber criminals may undertake.
Cyber vandalism may hit a business in the form of damaging system elements in order to interrupt its normal utilization. When this happens, a distributed denial of service (DDoS) occurs. A DDoS simply means that service from a business has been interrupted due to some form of digital vandalism. Cybercriminals may do this by developing and sending malware (malicious software) that disables anything from a computer’s hard drive to a server that stores information to specific programs or applications.
This type of attack could disable a company’s e-commerce store, for example, or inhibit employees’ ability to log into a computer network. While this type of vandalism is often done just to wreak havoc, some cyber vandals will hold company systems hostage until the company pays for their release.
Another example of a criminal committing cyber vandalism involves damaging computer hardware, such as when a disk drive is removed in an attempt to disable a computer system. This could happen internally by a disgruntled employee or externally from a thief attempting to steal company data or intellectual property. In this regard, not only does the company suffer the loss of equipment that damages a computer system or network, but the loss of important information can cause financial loss or loss of reputation.
Website defacement is a form of cyber vandalism that manifests itself by changing the look or function of a website. This can be something small, such as changing data on Wikipedia, or more complex. Individuals often deface websites to make a political statement or simply to draw attention or cause chaos.
Real cyber vandalism examples
2016: in the middle of the 2016 US presidential election, Donald Trump’s Wikipedia page was defaced several times by cyber vandals.
2016-2022: Activision-Blizzard had to deal with frequent DDoS attacks that made it hard to play many of its online-only games.
Hacking (Cyber Crime)
A commonly used hacking definition is the act of compromising digital devices and networks through unauthorized access to an account or computer system. Hacking is not always a malicious act, but it is most commonly associated with illegal activity and data theft by cyber criminals.
Hacking refers to the misuse of devices like computers, smartphones, tablets, and networks to cause damage to or corrupt systems, gather information on users, steal data and documents, or disrupt data-related activity.

A traditional view of hackers is a lone rogue programmer who is highly skilled in coding and modifying computer software and hardware systems. But this narrow view does not cover the true technical nature of hacking.
Hackers are increasingly growing in sophistication, using stealthy attack methods designed to go completely unnoticed by cybersecurity software and IT teams. They are also highly skilled in creating attack vectors that trick users into opening malicious attachments or links and freely giving up their sensitive personal data.
As a result, modern-day hacking involves far more than just an angry kid in their bedroom. It is a multibillion-dollar industry with extremely sophisticated and successful techniques.
Types of Hacking/Hackers
There are typically four key drivers that lead to bad actors hacking websites or systems:
- Financial gain through the theft of credit card details or by defrauding financial services.
- Corporates espionage.
- To gain notoriety or respect for their hacking talents.
- State-sponsored hacking that aims to steal business information and national intelligence.
On top of that, there are politically motivated hackers—or hacktivists—who aim to raise public attention by leaking sensitive information, such as Anonymous, LulzSec, and WikiLeaks.
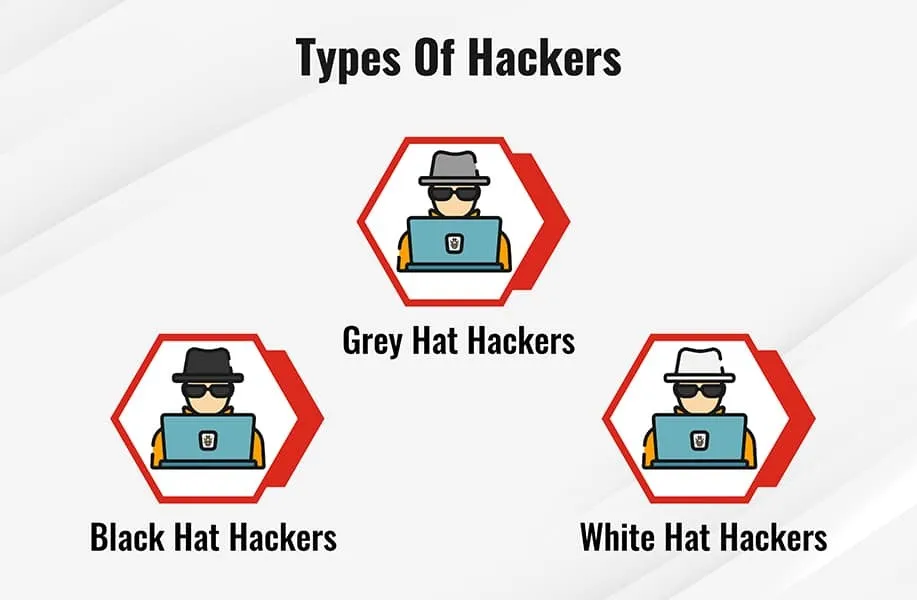
A few of the most common types of hackers that carry out these activities involve:
Black Hat Hackers
Black hat hackers are the “bad guys” of the hacking scene. They go out of their way to discover vulnerabilities in computer systems and software to exploit them for financial gain or for more malicious purposes, such as to gain reputation, carry out corporate espionage, or as part of a nation-state hacking campaign.
These individuals’ actions can inflict serious damage on both computer users and the organizations they work for. They can steal sensitive personal information, compromise computer and financial systems, and alter or take down the functionality of websites and critical networks.
White Hat Hackers
White hat hackers can be seen as the “good guys” who attempt to prevent the success of black hat hackers through proactive hacking. They use their technical skills to break into systems to assess and test the level of network security, also known as ethical hacking. This helps expose vulnerabilities in systems before black hat hackers can detect and exploit them.
The techniques white hat hackers use are similar to or even identical to those of black hat hackers, but these individuals are hired by organizations to test and discover potential holes in their security defenses.
Grey Hat Hackers
Grey hat hackers sit somewhere between the good and the bad guys. Unlike black hat hackers, they attempt to violate standards and principles but without intending to do harm or gain financially. Their actions are typically carried out for the common good. For example, they may exploit a vulnerability to raise awareness that it exists, but unlike white hat hackers, they do so publicly. This alerts malicious actors to the existence of the vulnerability.
Cyber Squatting (Cyber Crime)

Cybersquatting examples show Cybersquatting (a.k.a. domain squatting) is the act of registering, trafficking in or using a domain name in bad faith. Cyber squatters neglect the existence of a trademark to profit from others. In fact, domain names are cheap and are sold on a “first come, first served” basis.
As the internet started becoming popular, internet users knew businesses would need a website. Some users started buying domains to create sites that looked like they were from reputable companies.
Example: A cyber squatter could buy Heinz.com if the company hadn’t created a website yet, looking to sell the domain to Heinz at a later date for profit, or use the domain name to attract traffic and generate money through advertising.
If a business has a good reputation but no website, the company either pays the owner of the domain name to transfer the domain or contact a trademark attorney to start a lawsuit.
The second way is time- and cost-intensive, so trying to buy the domain directly from the cyber squatter is usually the preferred method. Today, opportunities for cyber squatters aren’t as common since most businesses make the purchasing of their domain a high priority, especially if they have a strong trademark.
Forgery (Cyber Crime)

It refers to the making of a false copy of a documents such as Birth Certificate, Driving License, Currency Note, Cheque Book, Passport, Postage Revenue Stamps and Marksheet etc. with an intent to check an individual or an organization. Special software, scanners, and other devices are used to regenerate these documents and act with the intended scam.
Cyber Extortion (Cyber Crime)

Cyber extortion is an umbrella term for a wide array of cybercrimes. Cyber extortion occurs when cybercriminals threaten to disable the operations of a target business or compromise its confidential data unless they receive a payment.
The two most common types of cyber extortion are ransomware and DDoS (Distributed Denial of Service) attacks.
Ransomware
Ransomware is a type of malware or “malicious software.” Malware is typically distributed via emails, infected websites, or fraudulent networks. Cybercriminals use these emails and websites to trick their recipients and visitors into clicking on infected links, thus downloading the malicious software. The software then proceeds to encrypt the victim’s files rendering their computers and networks unusable. The blackmailers then contact the victim, offering to decrypt their files for a fee.
DDoS attacks
In the case of DDoS attacks, multiple compromised computer systems attack a single target. The goal is to cause a denial of service, making the target’s network temporarily unusable. Depending on the target business, this website downtime can cause significant financial losses.
DDoS attacks and ransomware are often used in tandem. Cybercriminals often threaten businesses with DDoS attacks, claiming that the attack will occur if a fee isn’t paid to stop it. Cybercriminals also commonly threaten to publish sensitive or confidential data which could lead to lawsuits.
Cyber Terrorism (Cyber Crime)
There is no consensus definition for what constitutes cyber terrorism, according to the CRS.

In law, the closest definition is found in the U.S. Patriot Act 18 U.S.C. 2332b’s definition of “acts of terrorism transcending national boundaries” and reference to activities and damages defined in the Computer Fraud and Abuse Act (CFA) 18 U.S.C. 1030a-c. Interestingly, the CFA’s discussion of the “punishment for an offense” entails fines or imprisonment and suggests that it is a criminal act as opposed to an act of terrorism.
Some legal analyses define cyber terrorism as:
“The premeditated use of disruptive activities, or the threat thereof, against computers and/or networks, with the intention to cause harm or further social, ideological, religious, political or similar objectives, or to intimidate any person in furtherance of such objectives.”
This definition aligns with the Patriot Act and the CFA. Note that these provisions are criminal statutes and refer to individuals or organizations instead of state actors.
Defense analyst Dorothy Denning defines cyber terrorism as:
“Unlawful attacks and threats of attack against computers, networks, and the information stored therein when done to intimidate or coerce a government or its people in furtherance of political or social objectives.”
Her definition of cyber terrorism focuses on the distinction between destructive and disruptive action. As the Journal of Cybersecurity found, cyber terrorism causes responses similar to conventional terrorism, which seeks to “undermine civilians’ resilience by instilling a sense of fear and vulnerability opens in new window that erodes confidence in the ability of the government and law enforcement agencies to protect citizens against future attacks.”
Related terms include “cyberattack” and “cyberwarfare.” Cyberattack is a recent term that refers to activities conducted through information and communications technology, such as distributed denial of service (DDoS) attacks. Cyberwarfare is considered to be state-on-state action that is the equivalent to an armed attack or the use of force in cyberspace that triggers a military response.
Cyber security
Cyber security is the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. It’s also known as information technology security or electronic information security. The term applies in a variety of contexts, from business to mobile computing, and can be divided into a few common categories.
Computer – KnowledgeSthali


1 thought on “Menacing Cyber Crime | 1962 – Present”